Red teaming my iPhone (BART train safety)
Heads up: This post is outdated and/or represents a previous opinion of mine that has since changed. Please enjoy a look into the past, but don't link to it or reference it externally. Thanks!
Looking for my current writing? You can find that here.
Disclaimer: All content provided on this site is for informational purposes only and does not constitute professional financial or security advice.
Background
In the past two weeks, I’ve found myself a few feet away from iPhones being ripped out of commuter’s hands by thieves.
The first attack occurred during a late-night commute. The attacker entered the rear door of a sparsely populated train, ran down the aisle, and took a phone from a woman’s hand seated two rows away from me. He then exited through the front door of the train, onto the platform as the doors closed.
The second attack occurred during morning commute hours on a crush car headed into San Francisco. As the doors chimed and began to close, the attacker grabbed the phone from the hand of the commuter closest to the train doors facing the platform. The timing was quite impressive and there was no opportunity for the pursuit of the phone / attacker.
My take
From what I’ve observed, these bad actors will sit in wait on benches at stations in the East Bay and scope out commuters using smartphones, tablets, and laptops as trains approach the station. The bad actors prefer to attack cars chained in the middle of the train. This strategy provides a few advantages:
-
The middle cars often align with the station platform entry / exit stairs and escalators, providing an easy escape route once the device has been stolen.
-
Cars in the middle of the train host the largest flow of traffic in and out of the doors. During busy commute hours, there’s built-in obfuscation for their activities via a steady stream of commuters that blocks both other do-good commuters from intervening and the view from the in-car cameras that train operators constantly monitor.
-
Attacks against commuters aboard cars near the front and rear of the train introduce additional risk to the attacker in the form of increased vigilance from the train operators who are required to jut their heads out the control car’s window as train doors open and close.
In both attacks that I saw, the phones were snatched while they are still unlocked. Assuming that the bad actor is sharp enough to keep the screen on to prevent the phone from locking, they have gained full access to the phone and most of its apps / data.
The increase in frequency of these attacks, paired with the broader observation that no action performed on public transportation is private (I routinely see other commuters enter their banking application pin codes without feigning an attempt to hide the screen), provided me with a great opportunity to assess the situation and think through some attacks. Some questions to answer:
- What steps can I take to prevent my phone from being taken?
- If my phone was taken in a locked state, what actions need to be taken?
- If my phone was taken and the attacker had my global device passcode, what data / actions could they access?
Prevention
What steps can I take to prevent my phone from being taken?
I’ve put several new safeguards in place to lessen the chance that my phone is taken:
-
Ride in the first car, next to the train operator, whenever possible.
-
My phone goes into a zippered pocket on the approach to each station. The phone remains in my pocket until the train doors have closed and the train resumes forward motion.
-
No laptops out, ever.
-
No non-device passwords entered or sensitive emails opened on the train.
If my phone was taken in a locked state, what actions need to be taken?
- Immediately log into Find My iPhone and remote wipe the device. Accomplished via tethering a laptop to a mobile hotspot (if available) or by asking another passenger who witnessed the attack to use their phone.
If my phone was taken and the attacker had my global device passcode, what data / actions could they access?
Some basic prevention against this occurring:
-
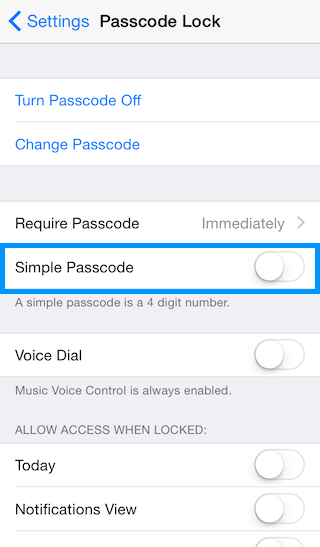
Require passcode immediately upon screen lock.
-
Disable “simple password.” To prevent reuse of the four-digit passcode used to unlock pin-based apps on my phone, I use a unique, extended-length (alphanumeric + special chars) for my device passcode.
Should the attacker gain access:
- Use unique pins for each passcode-protected app installed on my device. It’s worth noting that some companies are introducing non-standard (increased length or unique entry style) pins to their apps. Paired with 2FA, it’s a pattern I’d like to see furthered across apps that deal with sensitive data.
-
Logged out of Facebook and Twitter at the device level (could serve as an entry point to apps where I use social accounts for SSO).
-
Logged out of other apps that I use infrequently that contain sensitive data: Dropbox, on-demand services like Hotel Tonight, eBay, Airbnb, etc.
This minimizes the scope of access down to contacts, Mailbox, Google Calendar, and a few other sources of data should an attacker gain access to my unlocked phone before I can remotely wipe it.